OSINT Field Notes #2
From simple panorama how-to's and Starlink signals to drone footage, fake architects, and the digital fingerprints that expose hidden networks.
Welcome to the second edition of OSINT Field Notes.
Over the past month, I’ve been down a rabbit hole looking at the world after dark, using night-lights data to trace the scars of war, disasters, and power outages. Satellites see more than we realise, and those nightly patterns are quietly documenting how the world shifts.
This issue pulls together new ways to watch and interpret those shifts. From drones filming their own crimes to Starlink terminals fuelling scam compounds, each story this month looks at how visibility can cut both ways, exposing what others try to hide.
There’s also a practical teardown on making panoramas from videos without code, and a quick Google search trick to save you time in the field of niche discussion forums.
Thank you for all the messages after I launched the first edition last month. The response has been incredible and it’s motivating to see you are all using these techniques in your own work. Each and every day I learn more and more from this community and am inspired to pack in even more in these newsletters.
Ben.
1. Dispatches
These dispatches are a round-up of the most interesting open-source investigations, tools, and findings I have come across over the past month. These stories and tools show how researchers are mapping drone strikes, tracing recycled 3D assets, turning leaked archives into searchable databases, and spotting military build-ups from space, all using public data and a bit of creative analysis.
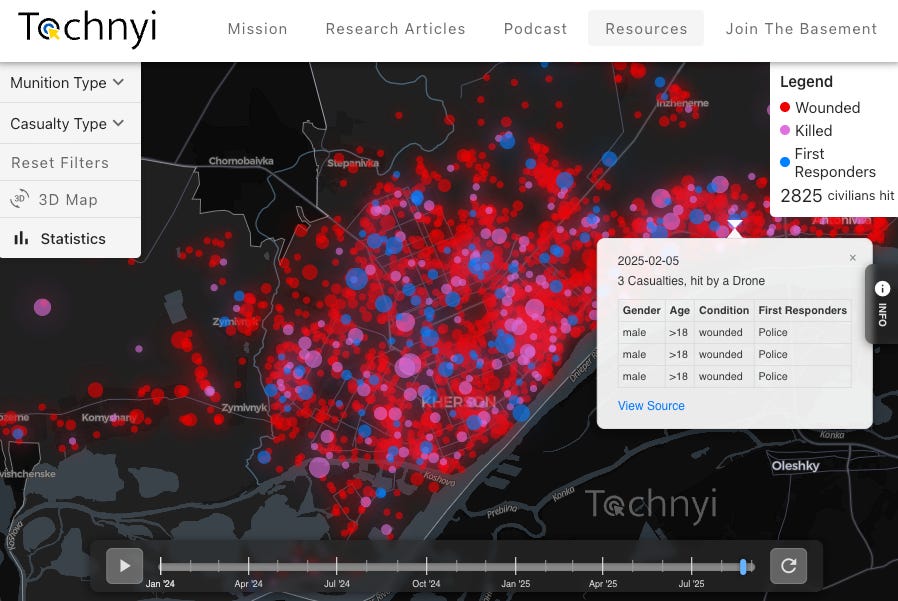
Drone War Crimes: Russia’s “Human Safari” in Kherson - Tochnyi Info’s new map visualises Russia’s FPV drone campaign against civilians in Ukraine’s Kherson, built from police records, prosecutor data, and footage shared by Russian soldiers. The data on the map also includes reports of shelling and unexploded ordnance. The project, led by researcher Brendan Kelley, shows how drone strikes on rescuers and civilians evolved into a deliberate pattern of terror across the city. This important work shows how open-source mapping and data verification can turn this horrific footage into a detailed record of systematic civilian targeting.
Propaganda in 3D: How IDF Animations Used Museum Assets - An investigation by The Ferret found that Israeli Defence Force propaganda videos reused 3D models from Scotland’s Irvine Maritime Museum, turning a boat-building workshop into scenes of Hamas tunnels and Iranian bunkers. The clips appeared on major news outlets before the museum pulled its scans offline. More visuals were identified in the thread here. This research shows how propaganda can be analysed to identify sources of content - in this case, innocent visuals that were repurposed to be used as visuals for narratives.
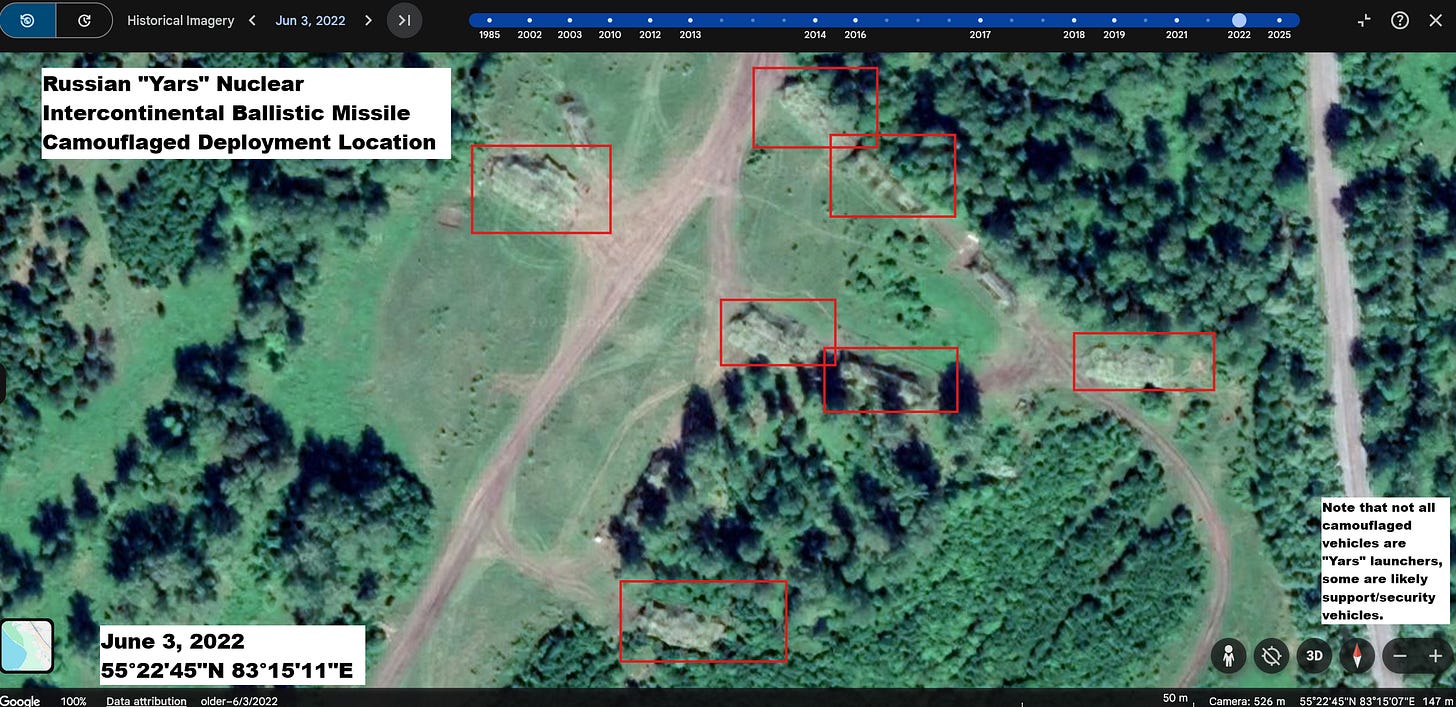
Redditors Geolocate Suspected Camouflaged Russian ICBMs - Users on r/GoogleEarthFinds noticed unusual shapes beneath camouflage nets during Siberian field drills and identified them as potential Yars missile launchers at coordinates 55.379345, 83.252542 in imagery on Google Earth from June 2022. The post was removed, but others saved imagery and compared it with earlier satellite passes.
PoliDashboard: A Look Inside Meta’s Political Ad Machine - An open-source app called PoliDashboard, from Toronto Metropolitan University’s Social Media Lab that tracks political, election, and social-issue ads across Facebook and Instagram. The team behind the app recently mentioned that their database of 3.5 million US political, election, and social issue ads on Facebook and Instagram, dating back to October 10, 2023, was now searchable. The database is useful as it allows researchers to discover who is running the ads and who they are targeting. The team have also mentioned that the data covers not just the US, but 30+ other countries totalling more than 10 million ads related to political, election, and social issues.
North Korean Scammers Turn to Architectural Freelancing - KELA traced a DPRK-run network using fake IDs, AI headshots, and generated social security numbers to win freelance architecture and civil-engineering jobs in the US. Files and screen recordings show pitches for permit sets, CAD drawings, and “licensed” stamps, plus GitHub-hosted persona kits with CVs, KYC docs, and hundreds of emails; WIRED verified details from the cache and interviews. This shows how sanctions-evasion is moving beyond IT into design work that can touch real buildings and infrastructure. It also shows how public freelancer profiles, repos, and file caches are key OSINT sources for detecting front companies and safety risks. For those that want to dig a bit more into the details of these, there’s a good thread on X here.
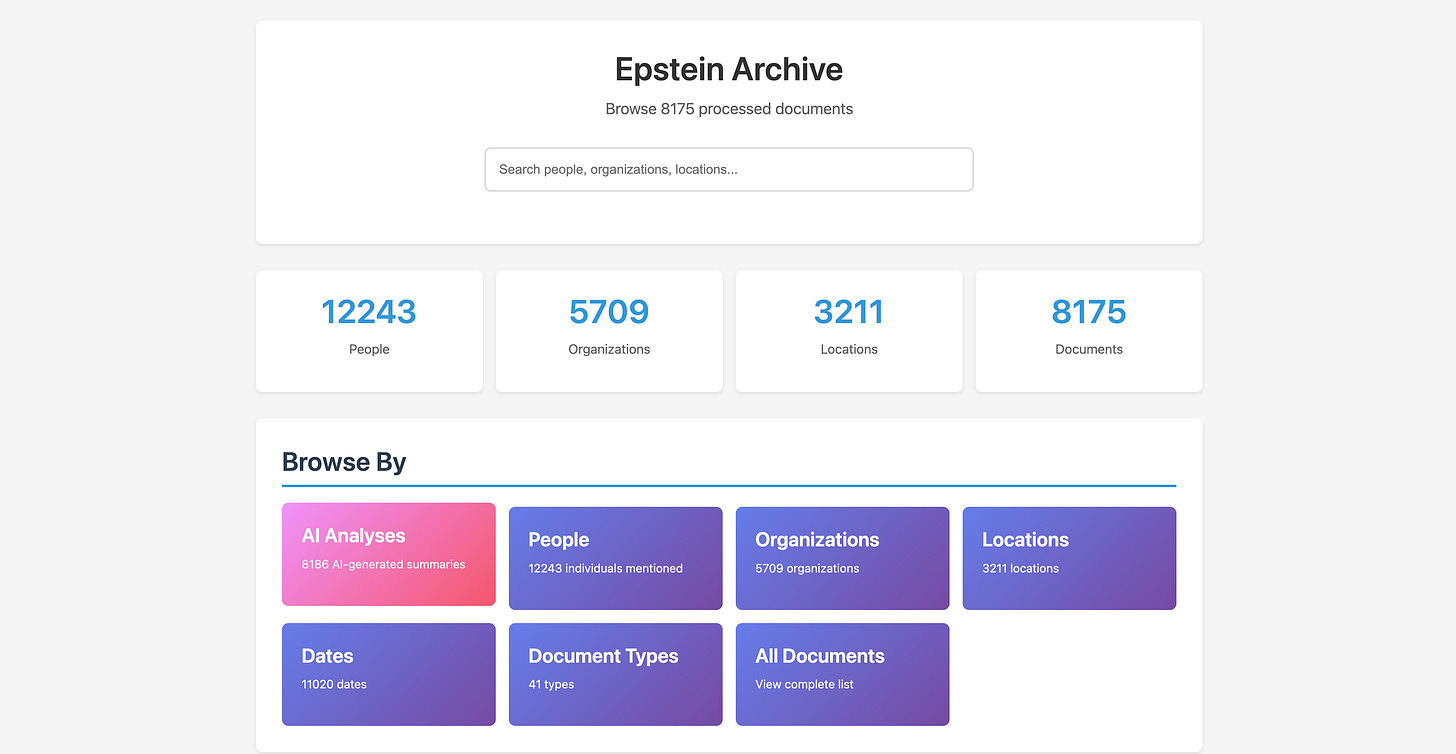
AI-Indexed Epstein Files Go Searchable - A Reddit user known as nicko170 used OCR and large language models to rebuild more than 8,000 Epstein-related documents released by the U.S. House Oversight Committee. The result, the Epstein Archive, transforms 33,000 disordered image files into a searchable database of names, organisations, and locations. You can find the Epstein Archive app here.
Tracking a U.S. Military Build-Up in the Caribbean - Reuters mapped a major U.S. buildup across Puerto Rico and the U.S. Virgin Islands using satellite imagery, ship and flight tracking, and on-the-ground photos. Upgrades at the former Roosevelt Roads base, new radar and tents, Reaper drones, and movements of warships and bombers indicate preparations for sustained operations within range of Venezuela. This is a great example of multi-source OSINT revealing intent and posture before formal announcements, from airport works and tents to ADS-B trails and commercial satellite passes.
Mapping Inequality: How Highways Erased Detroit’s Melting Pot - Segregation by Design used redlining maps and aerial imagery to show how 1950s–60s “urban renewal” and highway projects destroyed Detroit’s diverse Corktown neighbourhood, displacing thousands of Irish, Mexican, and Polish residents. I really appreciate this niche field of work, as it uses archival imagery to expose how infrastructure and policy decisions erased entire communities.
2. From the Toolkit
This month’s quick tool is a Google Search indicator I have enjoyed using which searches for a specific phrase in “forums” and “community” boards, posted by a member of that board, as indicated by “date joined” or “last post”.
inurl:forum OR inurl:community “PHRASE” AND (”date joined” OR “last post”)Simply swap out the word PHRASE for the word, or phrase that you are looking for, and run it in Google’s search bar. This works especially well if you are doing research on communities that might use coded-language or use group-specific terminology to reference subjects.
3. The Technical Teardown: No-Code Panorama Stitching
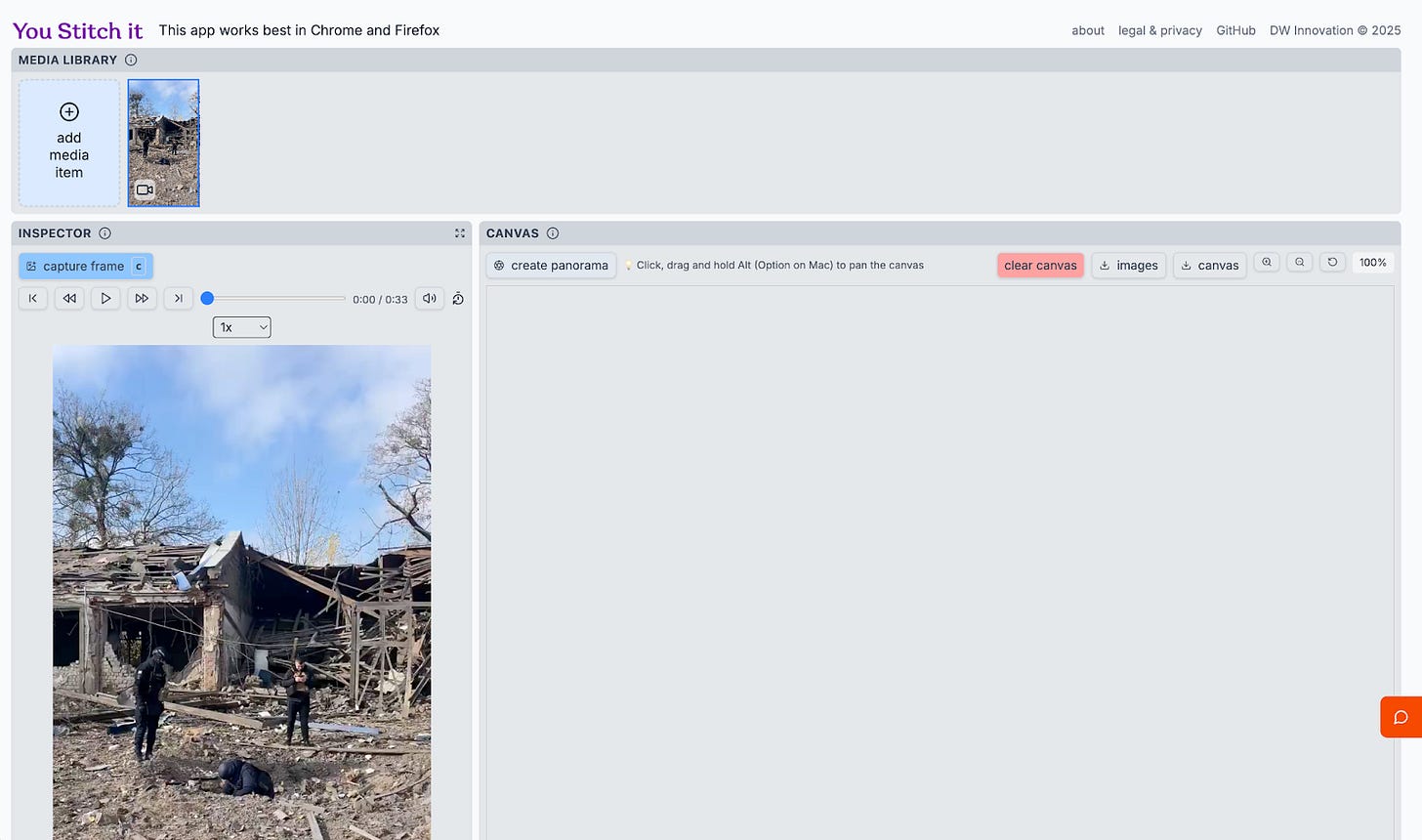
While there’s a few good attempts at AI-powered geolocation, nothing comes close to the power of a human being, especially in areas where there are very few elements to use geographical reference points. When analysing a video, though, I’ve found the most useful step for geolocation and analysis of a scene is to create a panorama, but creating that can be tedious and time consuming. So that’s where a little bit of automation can come in handy, and in this technical teardown, we’re going to walk through the use of a tool called You Stitch It
For this example, we’ll use a video of the aftermath of Russian bombings in Kharkiv.
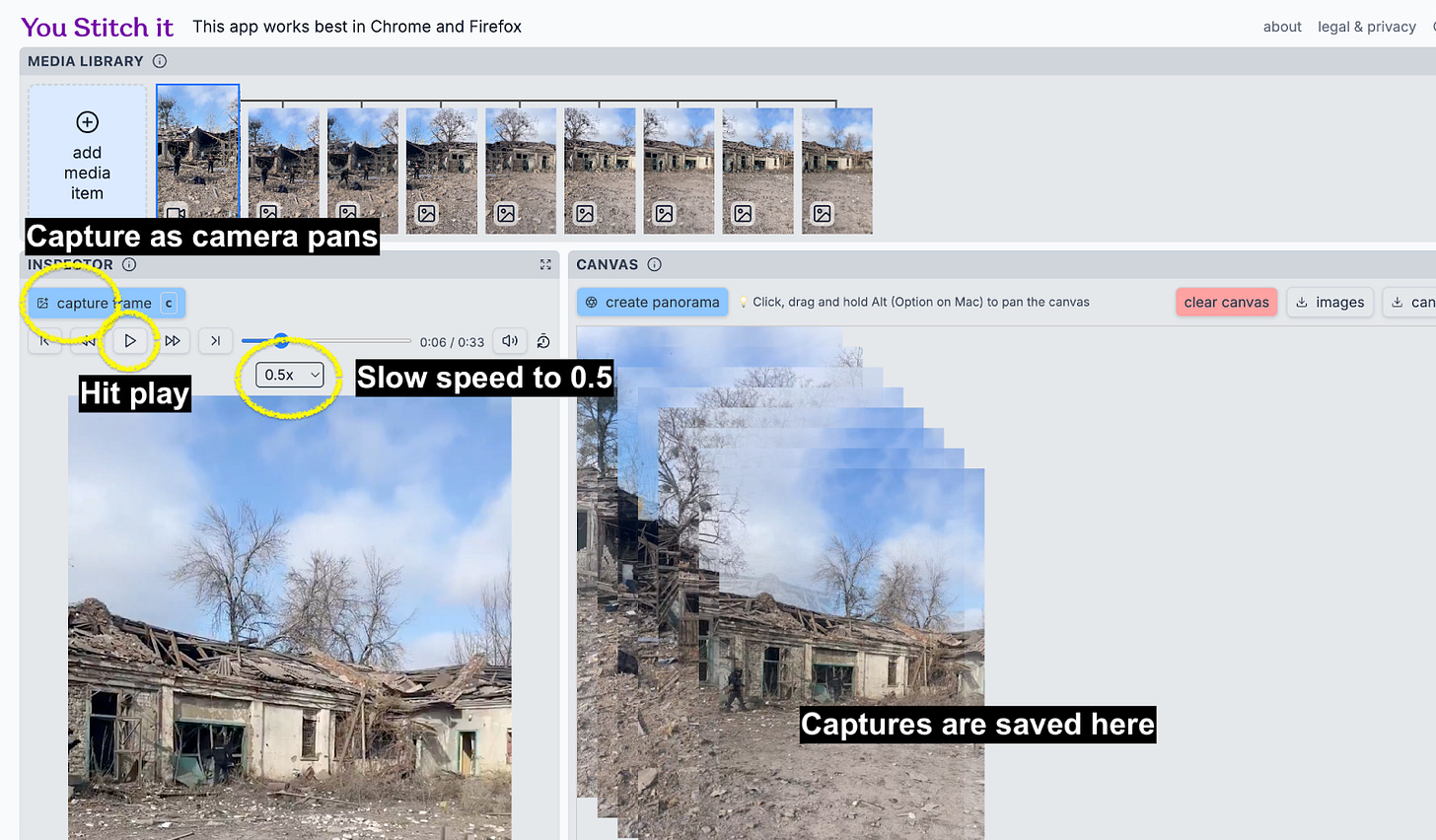
Step 1
Download the video and drop it into You Stitch It.
Step 2
Select the dropdown to play the video at a slower speed (I do 0.5) and press play. As the camera pans, click ‘capture’. The captures will be stored on the right side of the screen.
Step 3
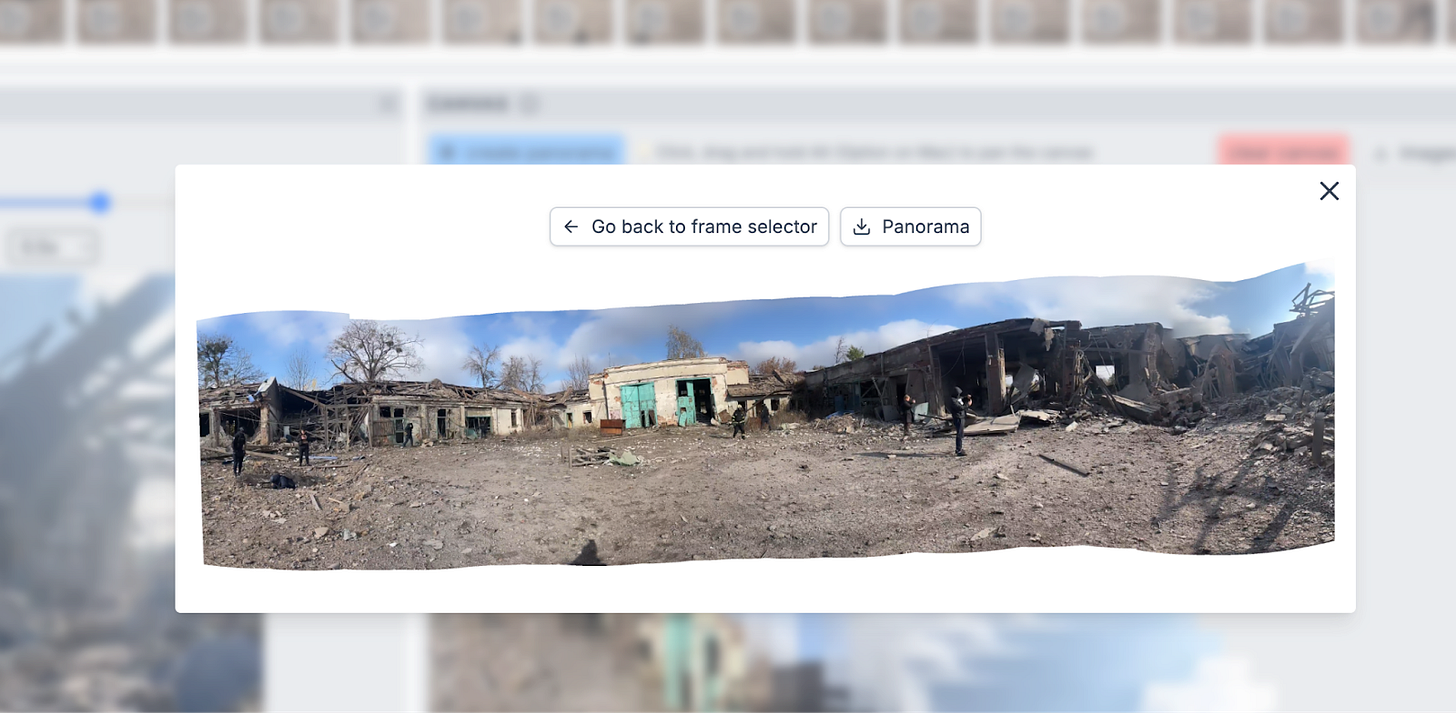
Once you have caught the view that you are after, and have sufficient coverage of the area in the video, click ‘create panorama’ and it will generate a panorama. This is generally quite quick, but depends on how many captures you have made. In this specific example it took a few minutes to load as I took a lot of screenshots.
You can download the image which opens it in full view, helpful for producing analysis reports, scene investigations, geolocation graphics or item and people identification.
Step 4
We’re not done yet. It needs to be geolocated. While tools like this are helpful, always remember to revert back to the source footage to confirm a location, as panoramas can lack depth of objects and are never entirely accurate. The coordinates for this location are: 49.93974, 36.42587.
If you look at the panorama and the geolocated site, you can see the difference in the layout of the buildings, a reminder that tools are never the final solution.
I chose this open sourced tool after seeing it posted by Julia Bayer at DW, and wanted to include this in the newsletter’s technical teardown as it’s a no-code friendly way of making a panorama. For those seeking a more technical and self-hosted form of panorama stitching, you can also check out Hugin.
I’d be amiss if I didn’t mention that panorama stitching is a growing field, with regular developments likely due to its applicability in the video production world. Last year, for example, VidPanos research was published, which takes video panoramas and turns them into widescreen videos that show the extent of the periphery camera vision.
By using a simple panorama stitching tool like the above, it removes the laborious time spent matching up frames in a manual panorama, or having to consistently slide a video when analysing it. As a secondary benefit, panoramas give a quick win when creating visuals for reporting or general location proofs.
4. Case File: Finding the Starlink Signal in Myanmar’s Scam Compounds
When Thai authorities cut electricity and mobile networks along the Myanmar border in February, it appeared that the region’s vast scam industry might finally lose its connectivity source. However, not long after the cuts satellite images began to show hundreds of new dishes appearing on rooftops. These were Starlink terminals, installed across compounds to restore internet access and keep operations running.
The compounds, many controlled by Chinese criminal syndicates, traffic thousands of people who are forced to run online scams. Workers are made to pose as investors or romantic partners to defraud victims around the world. KK Park has been widely reported on as one of the largest sites. Until February, it relied on power and internet from across the Thai border. When that was cut, the operators turned to satellite internet.
While the online scams have been the focus of the activities at the compounds, survivor testimonies and visual evidence have also documented how those trapped in the compounds suffered torture, routine beatings and were forced to live in appalling conditions.
Identifying the Starlink Network
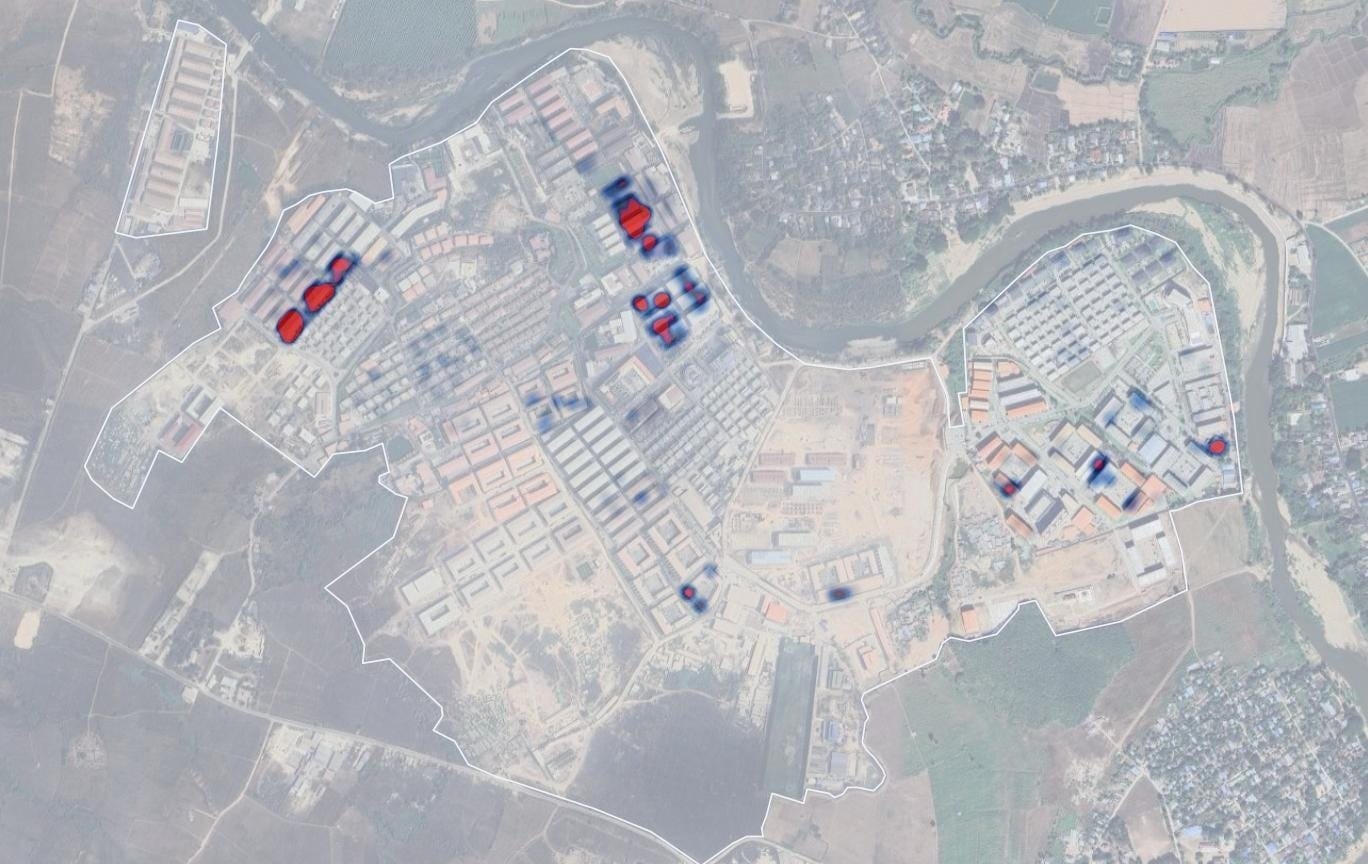
Investigators used freely available imagery on Google Earth to monitor the compounds after the shutdown. By comparing older and newer images, they spotted clusters of small reflective circles appearing on compound rooftops. The size, shape and orientation matched Starlink terminals.
These geospatial findings were then compared with on-ground photographs taken by AFP showing the same white dishes.
A heatmap created from the satellite imagery showed many more terminals spread across KK Park. This indicated that the operators had built an independent network just after the Thai restrictions. The evidence was supported by survivor accounts and local reporting that confirmed Starlink’s use to reconnect the compounds and allow the international scams to keep running.
The technique used to identify the dishes in KK Park was also used to identify similar rooftop patterns in satellite imagery from a compound near Lawksawk, almost 200 kilometres further inside Myanmar.
With the combination of Starlink terminals and diesel generators, operators no longer needed national infrastructure and could continue from more remote areas.
So what happened next? Well, following a series of reports on the presence of Starlink devices support ongoing scam operations within Myanmar, the military junta claimed they raided one of the compounds and uncovered a number of Starlink terminals (image below) and alleged they freed about 2000 trafficked workers.
Investigations group Myanmar Witness identified a number of images showing Myanmar Military dismantling Starlink devices on rooftops in KK Park.
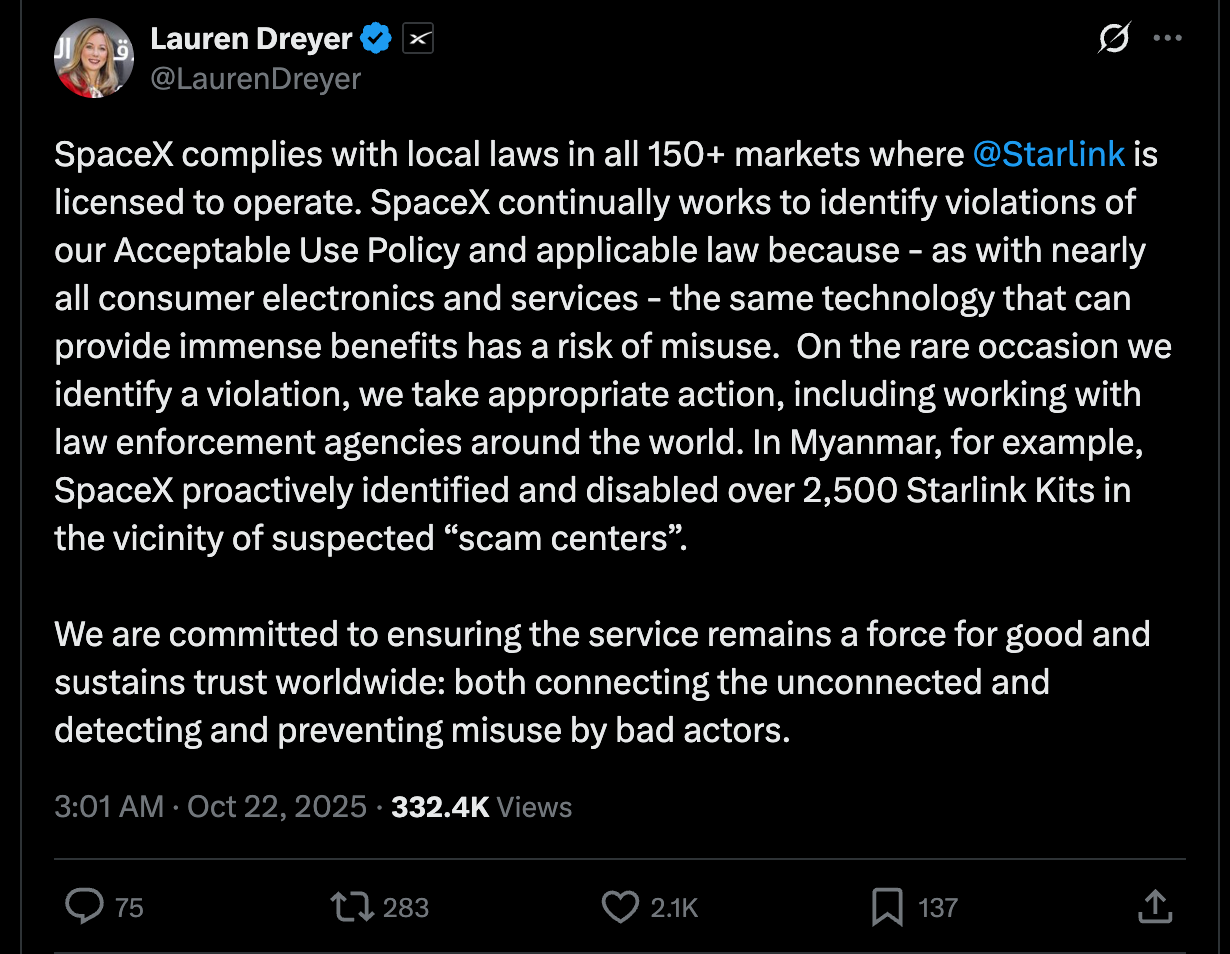
Following the raid, SpaceX confirmed it had disabled over 2,500 Starlink kits linked to scam compounds in Myanmar. The announcement came days after the military retook KK Park, freeing about 2,000 trafficked workers and confiscating dozens of terminals on site.
This investigation shows how freely available imagery and local reporting can uncover the infrastructure sustaining transnational organised crime, all through the simplicity of internet connectivity dishes on rooftops.
By tracing these signals, investigative journalists, open source researchers, and on-ground reporters helped expose a system that had operated beyond reach. Their findings fed into a wider understanding of how scam compounds stay connected and profitable, informing the actions now being taken by governments to target the billions flowing through this criminal economy. Even more important now, is the ongoing monitoring of what happens at these sites, and similar sites, now that the sanctioned Myanmar military junta has claimed to dismantled at least one of the sites.
Closing Note
This edition has covered a lot of ground, from drones that film their own crimes, to Starlink dishes keeping scam compounds online, to 3D assets quietly recycled in military propaganda. Each of these stories reminds me that OSINT isn’t just about finding data, it’s about seeing patterns others overlook.
Each small method adds another layer of clarity, helping us trace signals, verify stories, and map what matters. I’ll keep exploring more of these techniques next month, and I’d love to hear what you’d like to see covered next.
Ben.








Tochnyi Info’? You're seriously using a Ukrainian propaganda channel?
Completely destroys your "OSINT" credibility.
Why don't you try a Russian propaganda channel for balance?