OSINT Field Notes #3
3D scenes from scraps of imagery, X’s hidden location signal, how to follow sanctions paper trails and the global MAGA grifters exposed.
Welcome to the third edition of OSINT Field Notes.
Lately I’ve been buried in gaussian splatting, a technique that turns photos into 3D scenes. Skyfall-GS is the latest example, rebuilding terrain from angled satellite shots. It’s still rough, but you can already see the impact for understanding what has happened in an area, hard-to-reach incidents and explaining places most people will never visit.
This edition keeps that theme: taking scraps of information and turning them into something solid. The dispatches section looks at X’s new location data panel, Google’s Nano Banana for imagining ground and satellite views, sanction-evasion research tricks and a dataset of accounts posting from China on X. The Toolkit covers Air Loom’s 3D flight paths. The Technical Teardown walks through how to chase a sanctions story from a headline into documents. And the Case File looks at what X’s new location tag really shows when you zoom out to networks.
We’re at about 2,000 monthly readers now, which is wild for a third issue. Thanks for reading, being a part of this and letting me send this your way.
Ben.
1. Dispatches
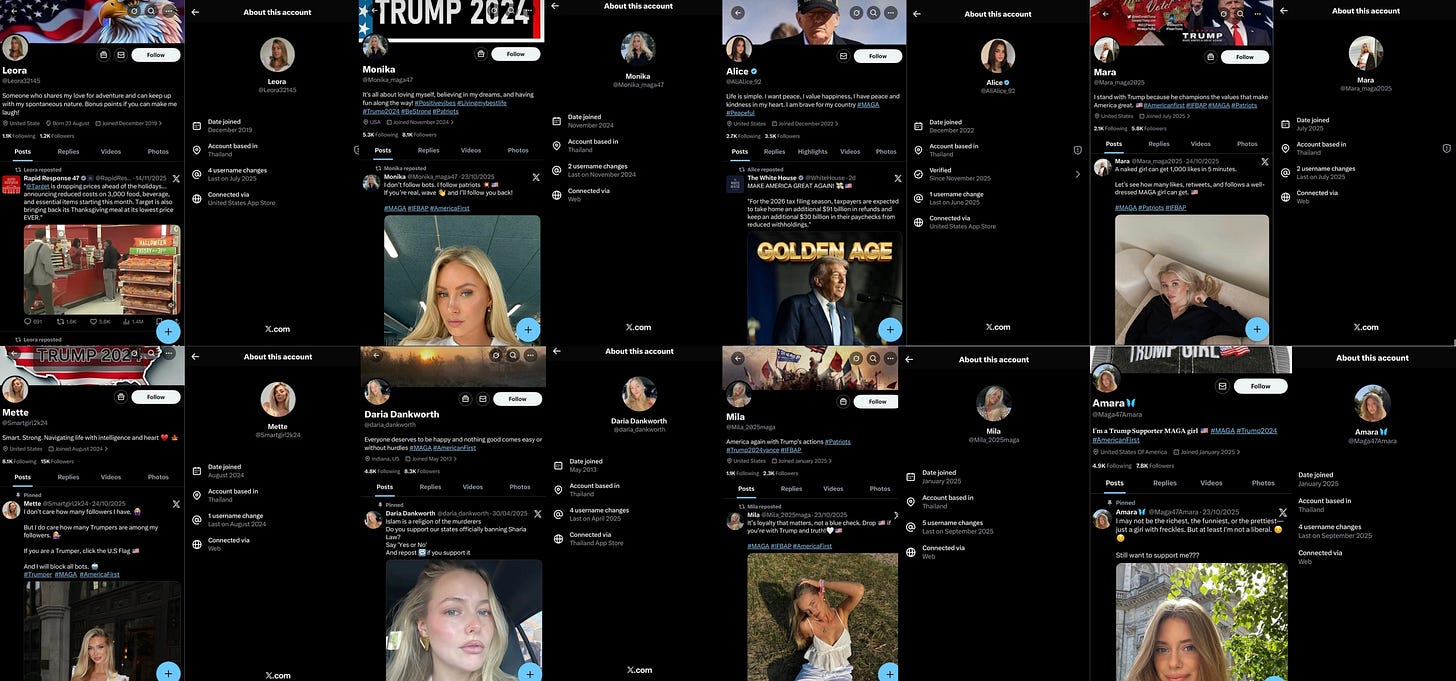
X’s “About This Account” panel becomes a new identifier - X rolled out the “About this account” panel on profiles that shows an apparent country or region and username-change history. Researchers have already used it to expose clusters of “MAGA” and “patriot” accounts that claim to be US-based but show locations like Thailand, Nigeria and parts of Southeast Asia, revealing a mix of influence work and engagement farming. For investigators, this is a useful hint rather than proof: something to screenshot, log and cross-check against posting times, language, image reuse and cross-platform identities before you treat any data as hard attribution, as covered in reporting from outlets like TechCrunch and the Guardian. I’ve dived a bit deeper into this in the ‘Case File’ section at the end of this newsletter.
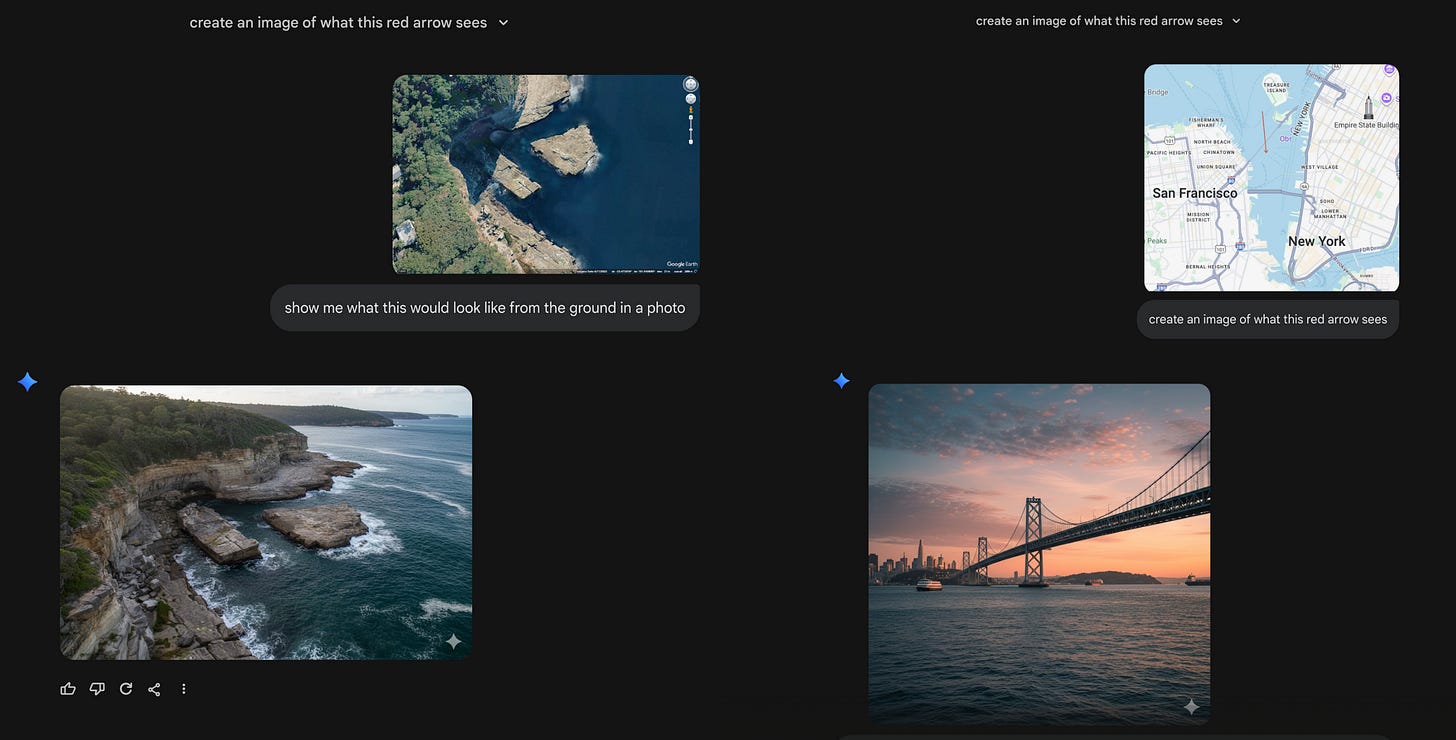
Google’s “Nano Banana Pro” for imagining ground locations from satellite data -Google’s Nano Banana Pro image model is now wired into Gemini. There’s a lot that Nano Banana can produce, so it’s likely it’s going to be used for entertaining, as well as nefarious purposes. But one application I have found very interesting is getting it to imagine what a satellite image would look like from the ground and equally in reverse, what a photo from the ground would look like on a map. Take a look in the screenshot below to get an idea of what I mean from a simple Google Earth satellite image and a Google Map screenshot with a red arrow. There’s more examples here.
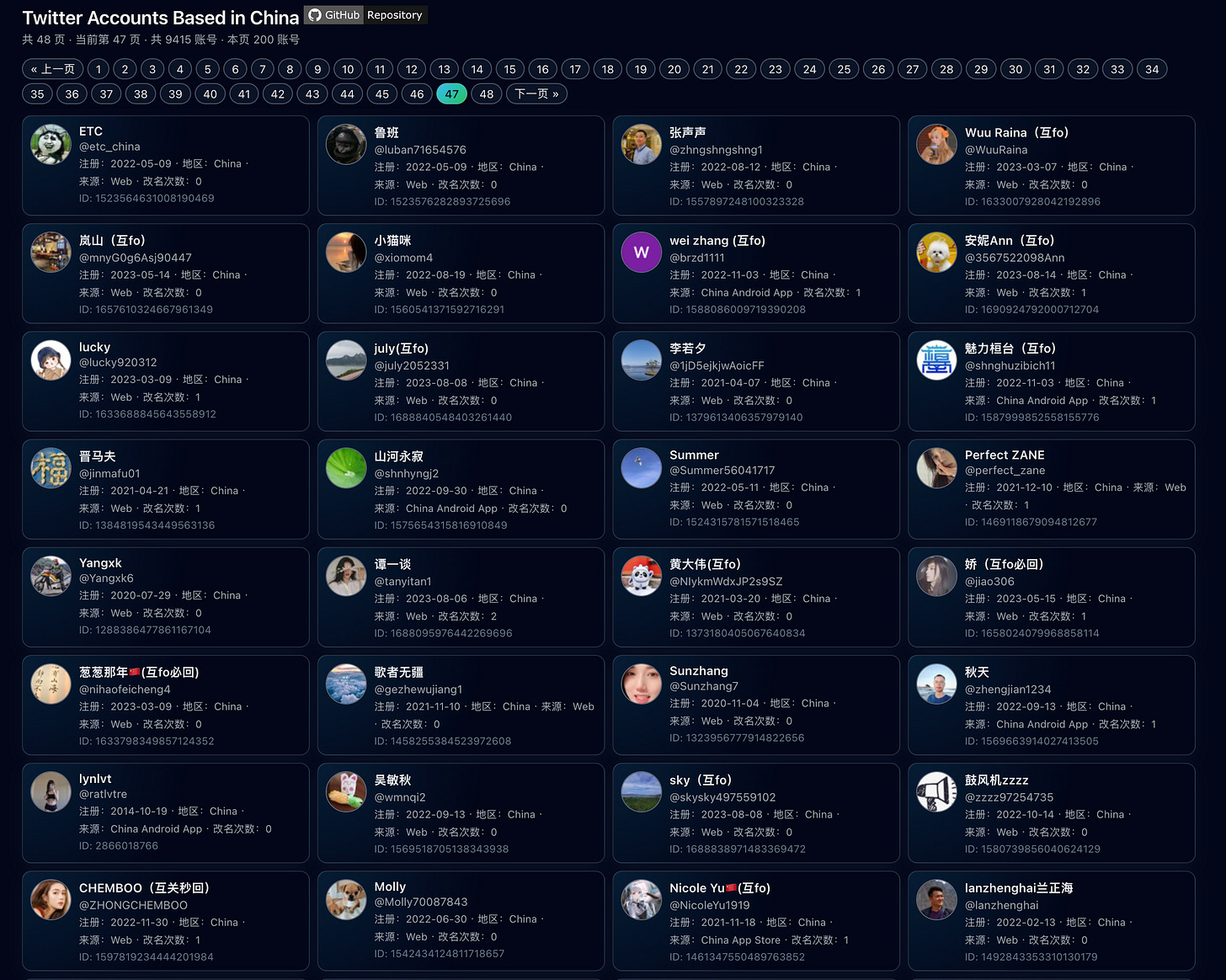
Mapping X accounts that report “China” as a location - GitHub user pluto0x0 has used X’s new location data to build a directory of roughly 9,400 accounts that report “China” in the “About this account” panel, including handle, join date, region, client type and username-change count. The site and linked repo have been shared widely as a quick way to scan profiles apparently connecting from mainland infrastructure despite restrictions on X. For research purposes, treat it as a seed list. Good for networks and narrative work, useless for proving who runs what without behaviour and other indicators.
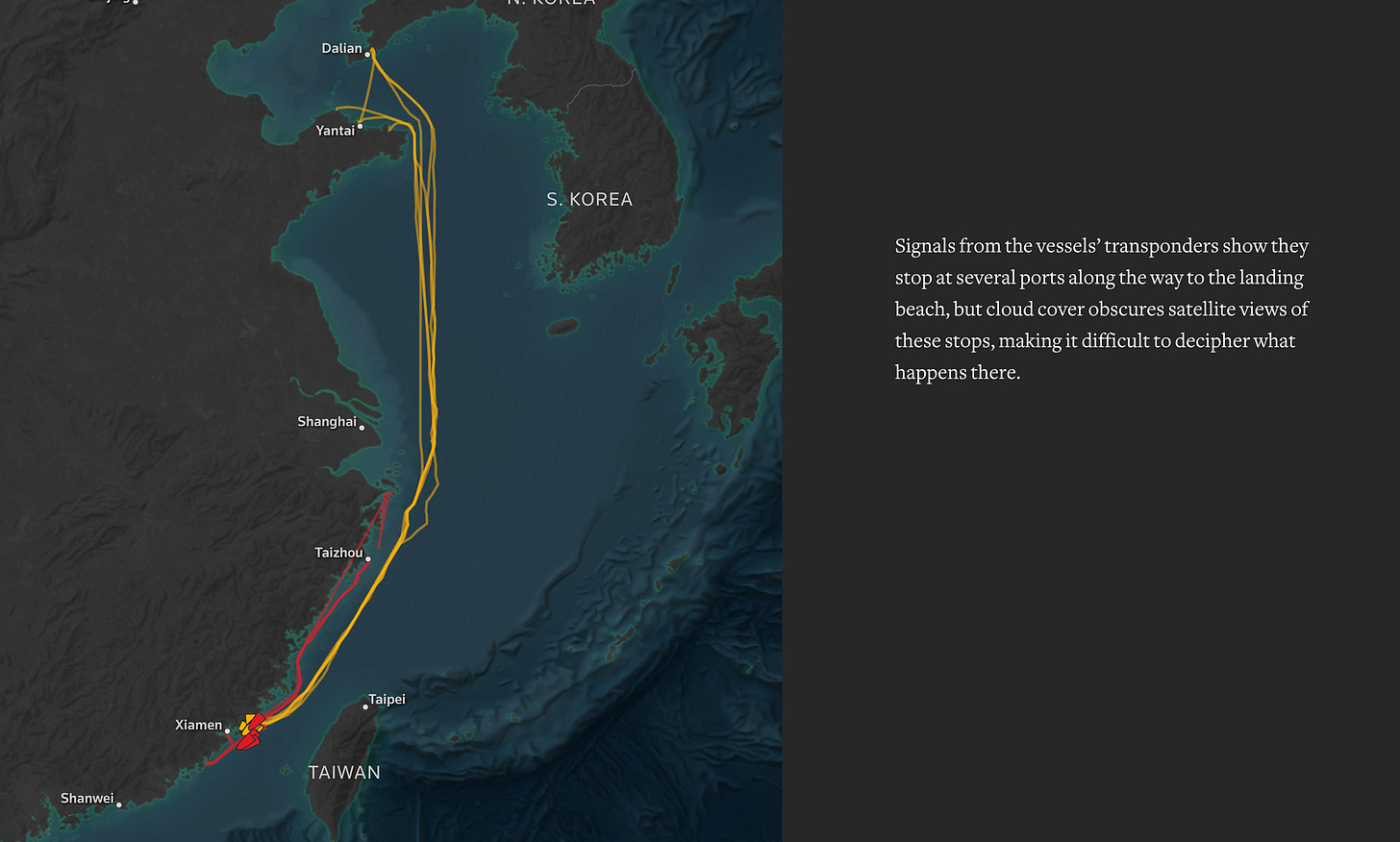
China’s “Shadow Navy” practises for Taiwan in plain sight - A Reuters investigation used satellite imagery, AIS data and Chinese state media to show how China is rehearsing a Taiwan invasion using a “shadow navy” of civilian ferries and cargo ships. Recent drills saw roll-on/roll-off ferries backing onto floating piers and unloading hundreds of military vehicles on Guangdong beaches, demonstrating how civilian shipping could be mobilised for large-scale amphibious landings. For analysts, if you’re watching Taiwan and China dynamics, civilian Ro-Ro ferries and pop-up piers need to be on your watchlist.
Lawfare’s “A7” laundromat and sanctions evasion at scale - In Lawfare, Elise Thomas lays out “A7”, a Russian cross-border sanctions-evasion network allegedly run by convicted money launderer Ilan Shor, which claims to have moved around 86 billion dollars. The piece shows how shell companies, crypto rails, obscure banks and Telegram “cash-out” adverts interlock to move sanctioned money around the system. It is a useful template for treating nested shell structures and Telegram money-service ads as parts of one graph and pivoting between leaked registries, court filings, payment processors and on-chain traces until you can see which entities are genuine nodes and which are just pass-throughs.
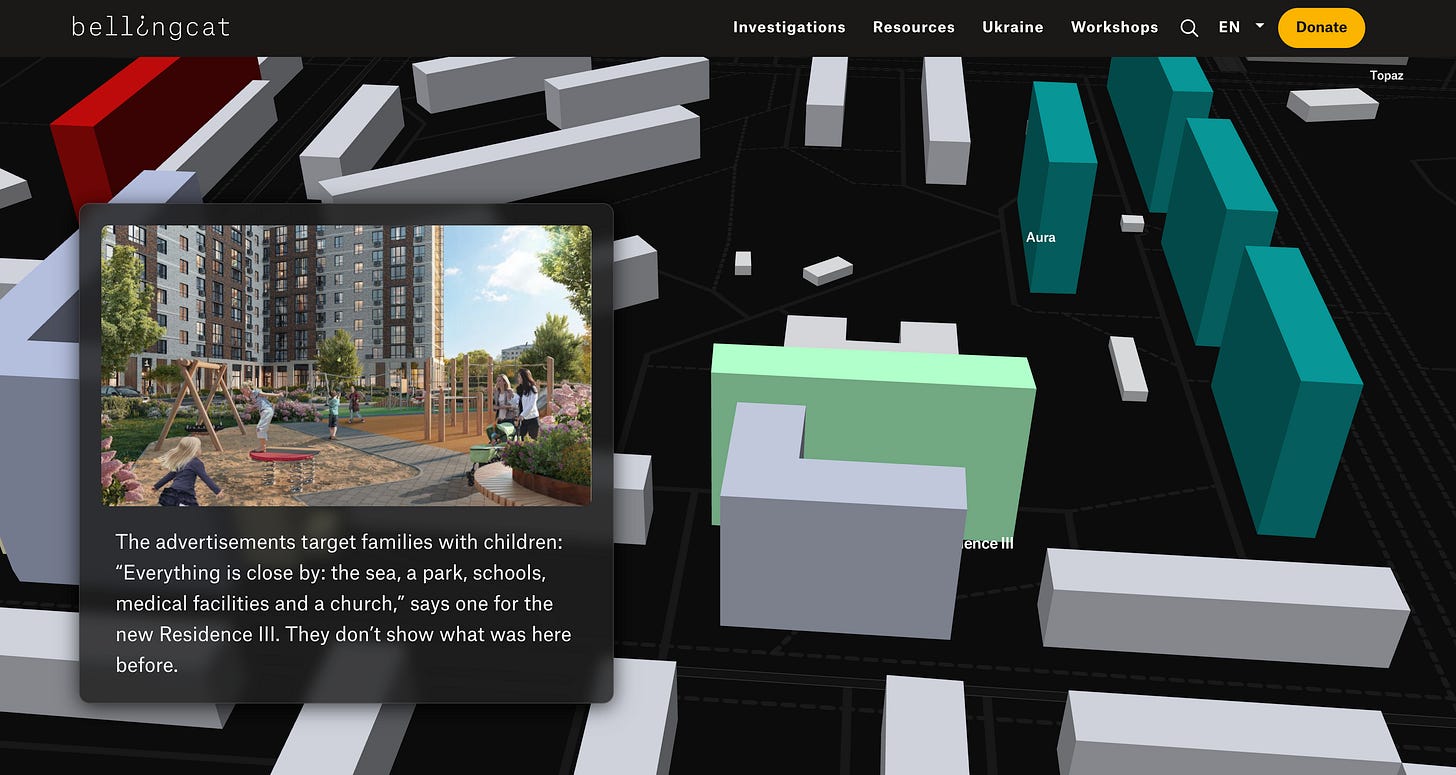
Russification of Mariupol documented through open source information - Bellingcat has mapped 23 new multi-storey housing complexes in the Russian-occupied Mariupol in Ukraine, with more than 50 buildings and at least 6,000 apartments marketed to Russian buyers on preferential loans. Using satellite imagery, Russian-language listings, ground video and documents, the investigation shows how Russia is rebuilding and repopulating the city while original Ukrainian residents remain displaced. It is a strong example of how time-series satellite imagery, property marketing material and residents’ posts can be combined to track demographic engineering.
2. From the Toolkit: Visualising Flight Paths in 3D with Air Loom
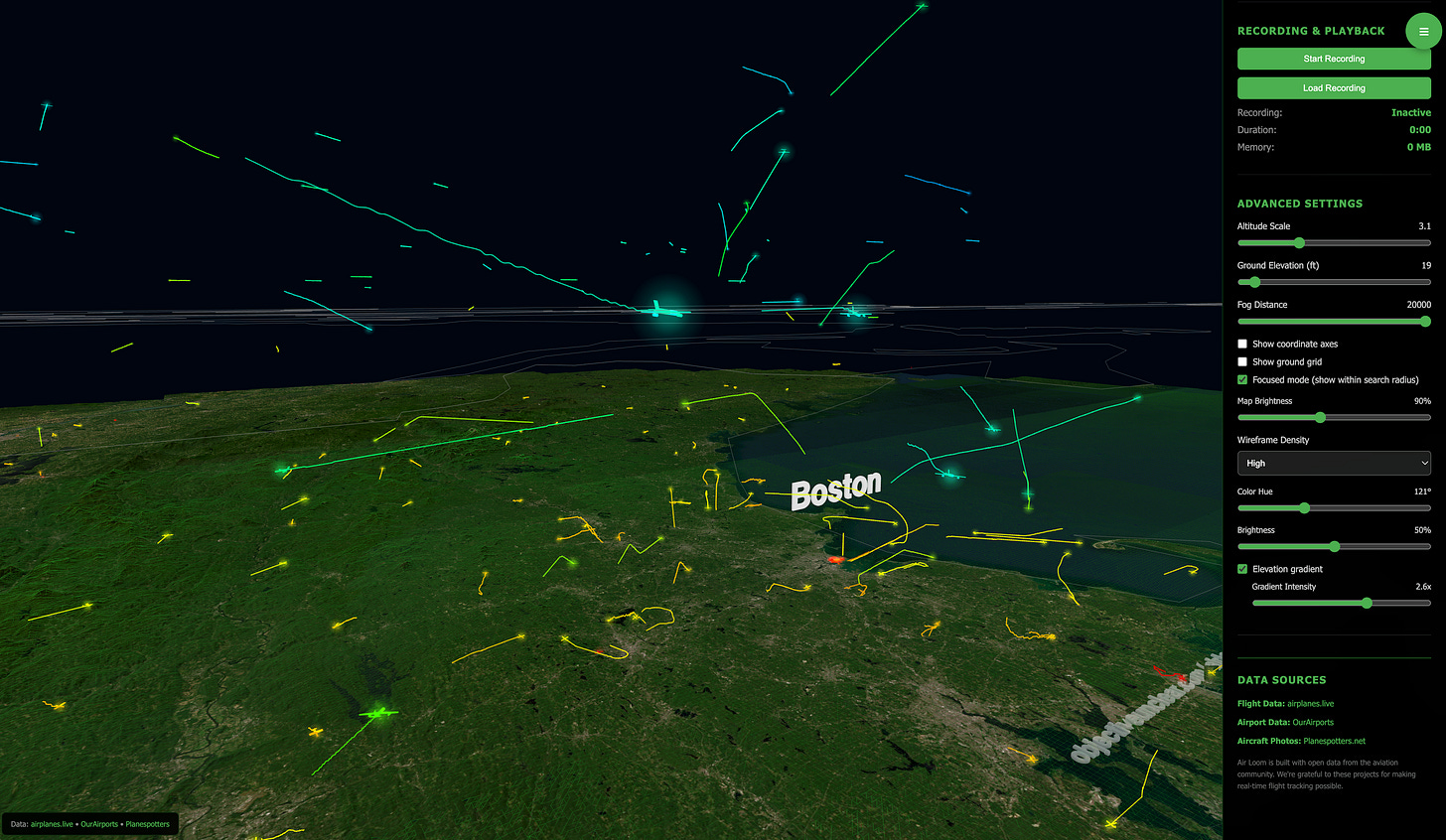
This month’s quick tool is Air Loom, a browser-based 3D flight tracker from Objective Unclear that pulls live ADS-B data onto a globe you can spin and fly through. Instead of flat lines on a map, you get ribbon trails coloured by speed or altitude, with search by airport or callsign, filters and a record or replay function over your area of interest.
For investigations, it is a visual layer on top of the usual flight trackers. You can record racetracks, holding patterns or low-level passes over specific sites. It is also a neat way to explain “that weird flight” to non-technical audiences, because people can literally see the aircraft flying through space rather than trying to imagine a line on a 2D map.
3. Technical Teardown: Following the Paper Trail Behind Sanctions Stories
When a big sanctions or seizure story drops, most of what matters sits in documents one or two clicks below the headline. The workflow starts with the media story, grab the key names and numbers, then walk down through legal documents, sanctions annexes and corporate filings.
For example, take the recent US–UK action against the Prince Group network. You might start with a BBC piece about a record bitcoin seizure and scam compounds in Cambodia. It gives you “Chen Zhi”, “Prince Group”, mentions pig-butchering schemes and hints at London properties, including a £100 million office building on Fenchurch Street. That list becomes your set of search terms.
Step 1: Go straight for legal PDFs
Instead of searching for “big bitcoin seizure”, go directly for “Chen Zhi” “Prince Group” site:justice.gov filetype:pdf. That leads you to search results with district court documents, including an indictment. The indictment shows how prosecutors say the scam compounds worked, how victims were recruited, which companies and exchanges are involved. It also hands you some great research terms: company names, project labels, cryptocurrency wallet addresses or internal domains.

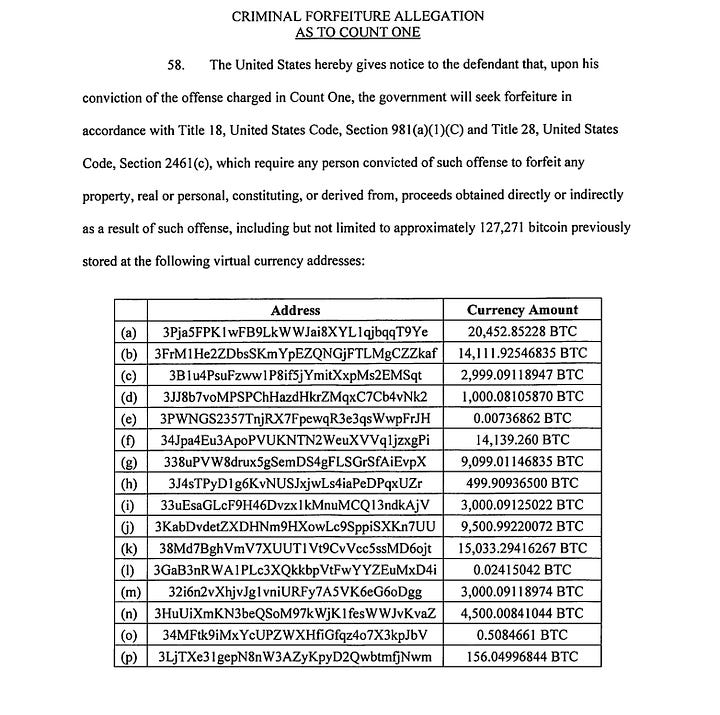
Step 2: Pivot into sanctions annexes
Next, move sideways into sanctions. Use the same names with a different filter, for example “Prince Group” “Transnational Criminal Organization” site:treasury.gov. That takes you to search results of the OFAC or Treasury press release and, crucially, the linked annex or chart. The annex lists everyone and everything newly sanctioned.
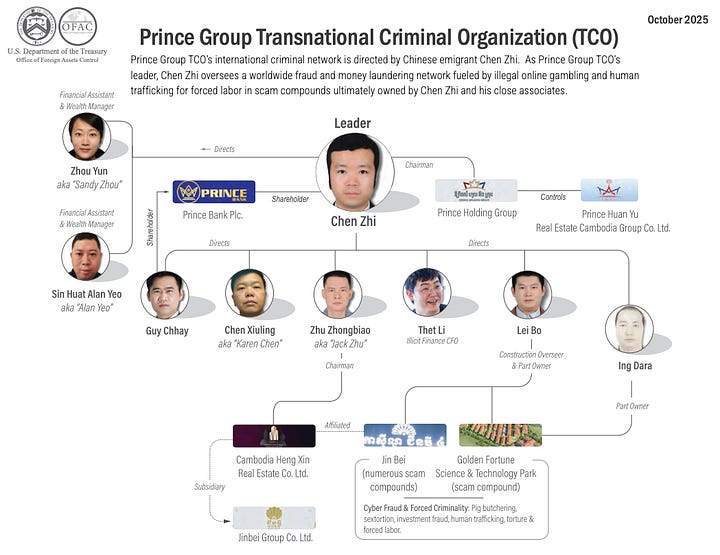

Step 3: Pull in other authorities
Then repeat the process with other authorities. For the UK, something like “Chen Zhi” “fraud” site:gov.uk takes you to a search result with the joint sanctions statement. While brief in detail, it includes some things others do not. In this case, it spells out that the network’s leader has poured money into London real estate: a mansion on Avenue Road, an office building on Fenchurch Street worth roughly 100 million pounds and a cluster of flats in New Oxford Street and Nine Elms. Now you have concrete assets, not just an abstract “network”.
Step 4: Use addresses to unlock filings
Those locations become your next pivots. Take “Fenchurch Street” and pair it with sale and purchase wording and file-specific search restrictions to narrow results:
“Fenchurch Street” AND “sale and purchase” AND filetype:pdf.
This surfaces a pdf document from Hong Kong stock-exchange showing the sale and purchase agreement of the property located at 6-12 Fenchurch Street in London for almost £100 million. The purchaser is listed in the document as ‘Retain Prosper Limited’, a company incorporated in the British Virgin Islands with limited liability.
Step 5: Confirm purchase and link
Now to pivot from our last result, use “Retain Prosper Limited” AND “Chen Zhi” in your search and you should be able to draw back to some of the sanctions lists from OFAC, Treasury Dept and others that list Retain Prosper Limited as a sanctioned entity linked with Chen Zhi.
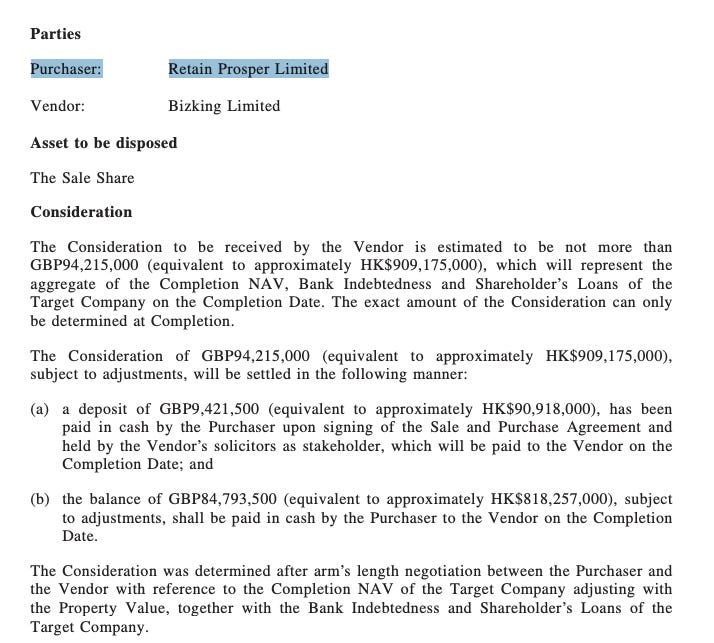
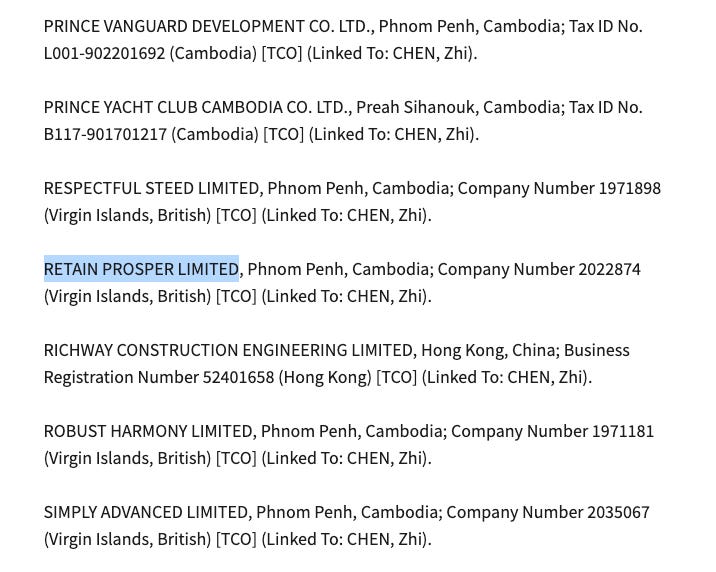
Step 6: Turn it into muscle memory
The same pattern works on almost any sanctions story:
Read the article and write down names, company labels, addresses and big numbers.
Use site:justice.gov filetype:pdf to find indictments and DOJ releases.
Use site:treasury.gov or site:ofac.treasury.gov for sanctions releases and annexes, then grab aliases and IDs.
Use site:gov.uk (and EU or others if relevant) for parallel statements that may list specific assets.
Take the addresses and values and search file-heavy domains like hkexnews.hk, sec.gov or investigate with filetype:pdf to surface sale-and-purchase agreements and circulars.
Use names “Chen Zhi” and entities “Retain Prosper Limited” to identify potential company links.
After you do this a few times, it becomes a habit. Don’t stop at the headline. Go dig the PDFs out.
4. Case File: X’s “About This Account” and the Hidden Geography Behind the Grift
When X added an “About this account” panel, it looked like a small change. Tap it and you get a region label, a main client and a bit of username history.
That little feature exposed something researchers had suspected for years. A lot of loud, very patriotic US political accounts weren’t posting from the US at all. Once the panel appeared, people started checking the big ones. “Ivanka News” with a million followers. “Trump Army”. Many resolved to India, Nigeria, Thailand, Eastern Europe. Anywhere but the US.
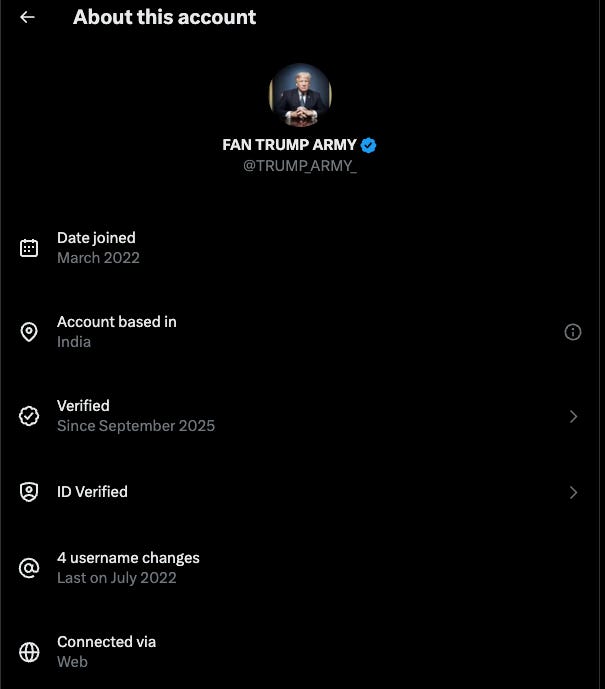
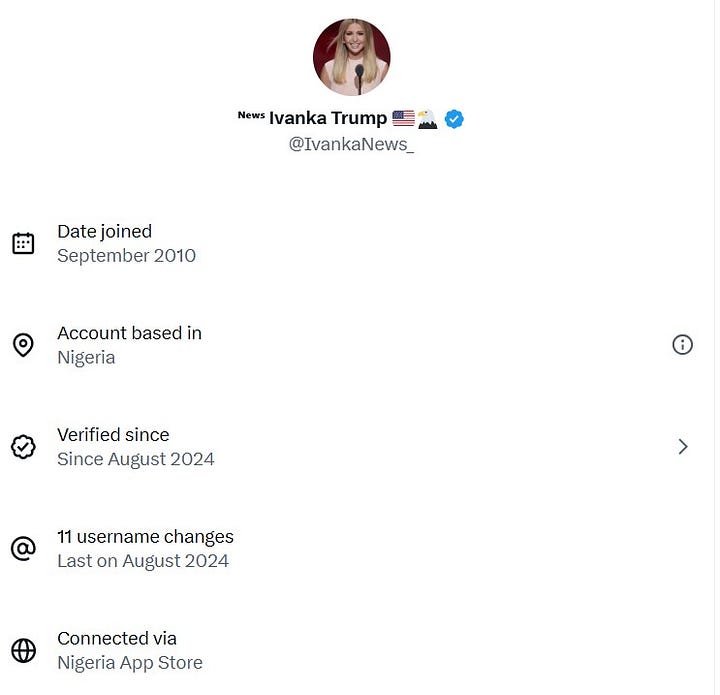
This even included a network of dozens of accounts claiming to be “independent MAGA women”.
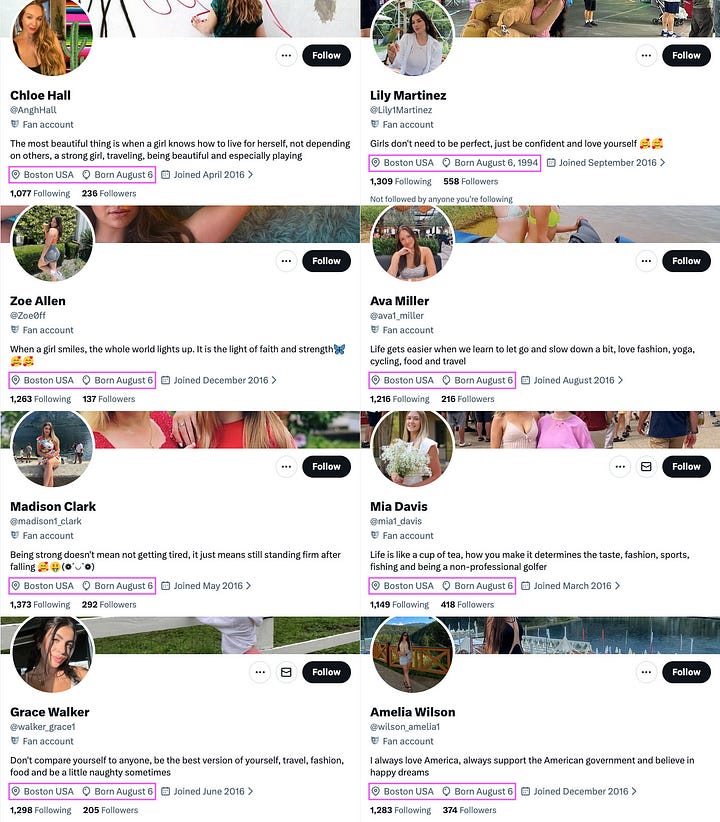
You could see the pattern in other clusters too. Researcher Sohan Dsouza confirmed suspicions of a South Asia network, and Bot Blocker flagged a batch of “Boston-based women, born in 1994” created within weeks of each other (images below show their work).

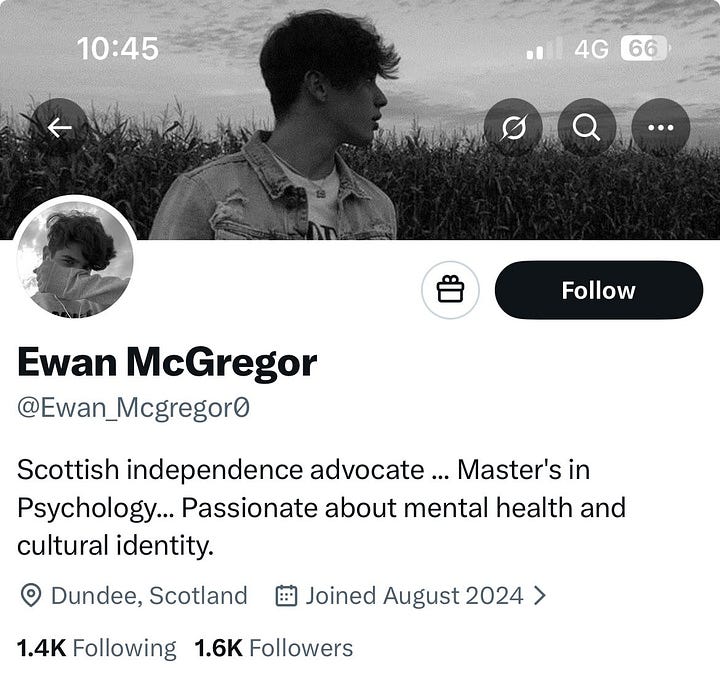
Then there were Scottish independence accounts that resolved to Iran.
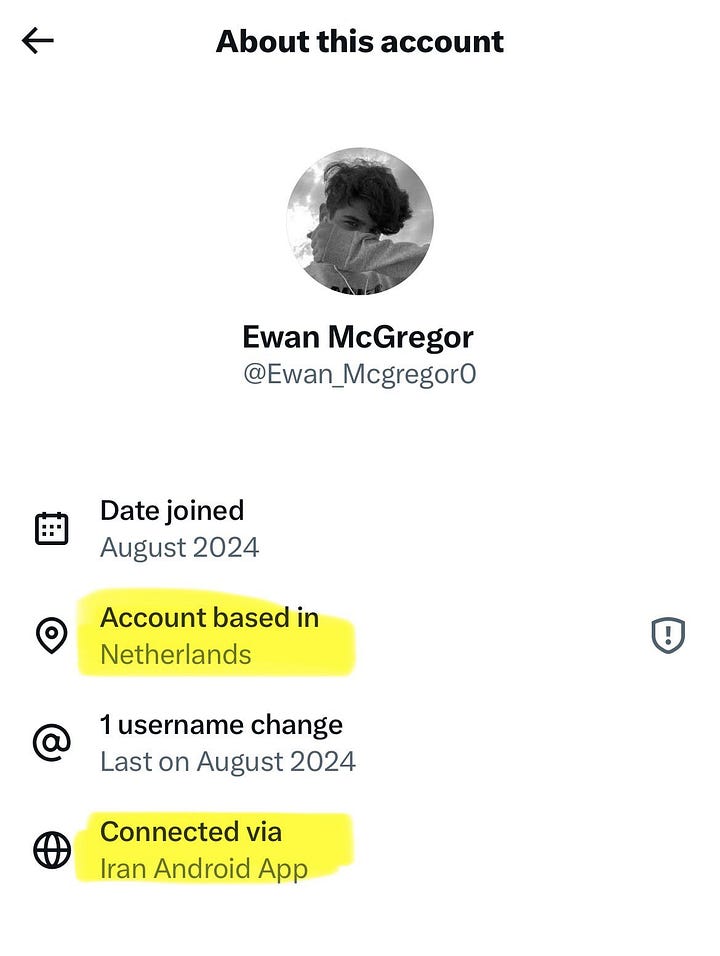
For researchers, the location data helps, but only as a weak signal. VPNs, travel and detection errors will bend it. People running coordinated campaigns, whether its for the purpose of influencing narratives, scamming or revenue farming, will learn how to trick it.
Plenty of real users will “look wrong” because they’re in exile, part of a diaspora, travelling or using privacy tools. An account posting about the US from Thailand might be fake, or it might just be someone who moved. You only know by looking at the whole account.
This is why it is so important to fold the location data panel into your normal checks:
Does the posting schedule fit the timezone?
Do the spelling and references match the claimed identity?
Does the username history look steady, or like a recycled account.
Where the feature really shines is at network level. If a cluster of near-identical political accounts suddenly resolves to Thailand or Myanmar, that’s a sign you’re not dealing with individual voters. Add the other indicators of inauthentic activity such as stolen photos, repeated captions, recycled memes and shared follower chains and you can call the network inauthentic with confidence.
Closing Note
If the sanctions teardown clicked with you, try the same steps on things you’re working on. The habits behind it are the same ones I used in a YouTube tutorial I made on searching for KML data, gold mines in Sudan and open security cameras. All of those through a few simple words typed into a search box.
Once you realise that a couple of smart search operators and public datasets can give you a clearer picture of almost anything, you start to use them everywhere even in your daily life from running, hiking, travel or just exploring your own city.
I am keen to keep shaping this newsletter around what you actually need. So if there is a topic you are interested in, a workflow you’ve found useful, or a tool you are excited about, hit reply and tell me. That is what drives each issue of OSINT Field Notes.
See you in the next one, Ben.



It was a thrilling read! 🍻 Thank you! 🙏 😊